The Video Game Crash
by Justin
Posted on 30-11-2020 03:21 PM

In 1983, the north american video game industry experienced a major “crash†due to a number of factors, including an oversaturated game console market, competition from computer gaming, and a surplus of over-hyped, low-quality games, such as the infamous e. T. , an atari game based on the eponymous movie and often considered the worst game ever created.
Similar to Hungry Shark Evolution
#11 edited by zarulhairee
member since 2008 • 50 posts
hungry shark evolution cheat codes [free] coins and gems for more coins and gems download windows 10 7 hungry shark evolution cheats that actually work 2020 today, the latest mod apk ios has gone out and prepared to download now. Our team finished this new cheat and they’re prepared to give it to you.

Hungry shark evolution is a two-dimensional action game in which you control a shark roaming the coast and driving humans and other marine animals into a panic as you unleash your hungry fury. You can choose between five different types of sharks, like the great white, the hammerhead, and the tiger shark. And you can even personalize your shark with tons of different items, like wigs and armored vests.
Evolution games are simulator games about evolving animals and the development of living organism. Feed and evolve a monster and check its development and survivability in exiting online fights. Control a tiny moving cell which becomes a big hungry shark and show the power of animal evolution in practice. Or change the genes of humans in your lab and create dangerous mutants. The plotting biologists here at silvergames. Com have put together the best free evolution games you can find online.
Times and seasons have changed. The time when you couldn’t enjoy hungry shark evolution due to insufficient resources are over. Now you can enjoy hungry shark evolution the way you want, thanks to this hack, which enables you to have as much resources as possible. Receive unlimited gold & gems to play hungry shark evolution.
Take control of a very hungry shark in this action packed aquatic adventure. Survive as long as possible by eating everything that gets in your way. Many different sharks to collect and evolve, including the hammerhead, great white and megalodon. Features: + console quality 3d graphics + 11 shark types to unlock + a huge free-roaming world to explore. + intuitive touch or tilt controls + 15 sunken treasures to discover + over 70 missions to complete + equip your sharks with special gadgets and items + unlock baby sharks to boost your predatory powers + combo bonuses and gold rush to beat your hi-score hungry shark evolution is regularly updated with new features, content and challenges to keep you coming back for more. Play as much as you like. No arbitrary time loops or energy mechanics. Game of the year 2013. (tiga awards). This app contains in-app purchases which allow you to buy gems and coin currency which can be spent on upgrades and accessories. Gems and coins can also be collected in game without requiring purchase.
Status: online your message was successfully sent! proof about the game the hungry shark evolution is a game that is played in the form of sessions. A session needs to be started by pressing on the "play" button. Every game session begins with a shark chosen by the user. The shark is seen to falling from somewhere in the sky, into the water. The aim of the player in every session is to be able to survive for the longest possible time along with earning points. This is made possible only when the player can battle and eat up a huge number of different creatures that come across. The boundaries of the game area can be seen through the maps.
Downloading hungry shark evolution_v8. 1. 0_apkpure. Com. Xapk (100. 1 mb) the xapk (base apk + split apks) file, how to install. Xapk file? this release comes in several variants, see available apks if the download doesn't start, click here videobuddy - youtube downloader 1. 54. 14. 8. 8291. 2. 0. 22. 114 communication 167. 0. 0. 24. 120 social 297. 0. 0. 36. 116 social 22. 5. 28-16 [pr] 339926180 tools 7. 83. 0 build 25 35223 entertainment lulubox - allow you to unlock all skin of freefire apk.
Evolution will always keep on going.
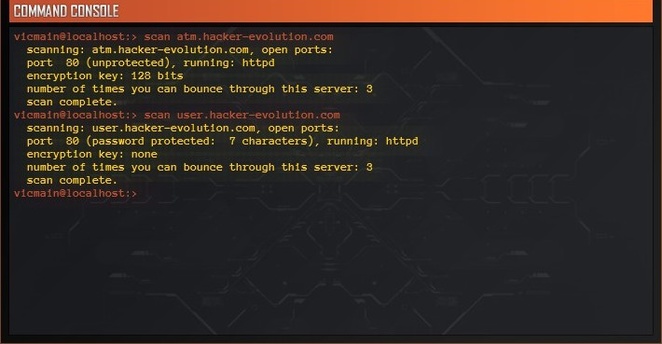
Hacker evolution es una intrigante aventura informática en la que el jugador, en el papel de un agente del servicio de inteligencia, tendrá que averiguar cuál ha sido el detonante de una cadena de eventos que ha dejado al mundo sin servicios básicos a través de internet. Durante el juego tendremos que hackear ordenadores rivales, robar dinero de cuentas bancarias para mejorar nuestro equipo, intentar encajar las piezas un enorme puzle, y por supuesto averiguar qué ha ocurrido.

Hatterene, grimmsnarl , and their evolutionary families can be considered counterparts. Both are generation viii pokémon evolving once at level 32 then at level 42. Hatterene and its pre-evolved forms are female only, while grimmsnarl and its pre-evolved forms are male only. Their final evolved forms are both fairy-type pokémon with identical base experience and catch rates, and each pokémon in each evolution line have the same base stat total as their counterpart (e. G. Hatterene and grimmsnarl both have a base stat total of 510). Both pokémon also have a gigantamax form, a signature g-max move, and use their body hair as their primary weapon. In addition, both pokémon are based on mythical beings from european folklore and mythology: hatterene resembles witches, and grimmsnarl resembles trolls, ogres, and goblins. Lastly, both are the signature pokémon of one of the rivals from pokémon sword and shield : bede for hatterene and marnie for grimmsnarl.
Duel evolution is a free trade card mobile game adapted from anime 'yu-gi-oh!', it's available on pc & mobile devices. Faithful reduction of huge cards and free construction of individual card deck. Let's duel! this game won't disappoint you! show full description.
A fork of {{sketch. Parentsketch. Title}} by {{sketch. Parentuser. Fullname}}. This is my evolution simulator! i uploaded some videos of this simulator to my youtube channel carykh: https://www. Youtube. Com/watch?v=gofws_hhzs8 it runs about 3x faster in the java version. Also: the js version might have trouble drawing rectangles. If that happens, disable hardware acceleration in your browser.
The features of the pro evolution soccer 2019 are as follows.
They yell like humans, climb trees and even mountains. Yes, goats are crazy creatures for sure. What would happen if mutations started happening to them? combine goats to evolve them and discover their most curious, exotic and bizarre forms! from the guys that couldn’t resist releasing yet another nonsensical sequel to cow evolution and platypus evolution, comes… guess what… goat evolution! come on, goats are rad.
No other pokémon have the same egg group combination as trevenant and its pre-evolution. Trevenant and its pre-evolution were designed by james turner.
Digimon Story: Cyber Sleuth – Hacker's Memory
Botamon is #4 in digimon story:cyber sleuth and is at the training i level. It is a free type, neutral attribute, has no equip slots and uses up 2 memory. It's special move is bubbles; it does not learn any inherited skills. Botamon can digivolve into koromon and wanyamon. Its support skill is innocent eyes which increases acu and eva by 1%.
Hungry Shark Evolution for Windows 10
Hungry shark evolution, a game from popular game developer studio ubisoft entertainment in the arcade category with the accessibility over ios and android. It is free to download game; however, it offers the in-app purchases option. It is quite helpful in getting resources. There are two currencies offered in the game. First currency is coin which is primary and second one is gem. Gems are premium and hard to obtain. It can be tough to progress without it but in-app purchases can help just as hungry shark evolution hack can do it. There are many more benefits of it and you will love to use so let’s get started now with benefits.
Hello guys! before getting to the hungry shark evolution hack, we would like to talk a little bit about the game for those that are not much familiar with it. The developers, are commonly known for their few ultra popular games but from what we are able to see, hungry shark evolution will most likely beat everything up!.
Hungry shark evolution (mod, coins/gems) - manage eternally starving shark and tires her hunger in many different ways. Eat fish and attack people, collect coins and perform daily tasks that will give you the opportunity to discover more new species of sharks, travel to a large and open ocean, looking for food, and enjoy quality and beautiful graphics hungry shark evolution mod apk. The deeper you swim, the more production you will get, but be careful, because the sea is full of other predators do not become dinner for someone!.
The best benefit of this specific hungry shark evolution hack. We want to provide hungry shark evolution cheats which are legitimate. The actual company is trying to pressure you to shell out real money – this is the only downside of the game. Yet you could definitely keep away from that by utilizing hungry shark evolution hack tool. There is an honest amount of game titles in which you are able to power ocean beings.
You were on thousands of sites already looking for working hungry shark evolution hacks, but everything you encountered was fake? then you are in the right place on the right site! this free online hungry shark evolution hack i am providing is 100% working, legal, and free. I have been a skilled game application coder for several years and know the ins and outs of the games.
Best Pokemon Games for Nintendo DS
Welcome and see our compilation of pokemon gba rom hacks. Though there are hundreds of these games exist online, we add only those games we think worth to be shared in the community. Gba rom hacks are the choice by most gamers, but it doesn’t mean you should ignore the other pokemon rom hacks.
Pokémon evolutions by Friendship
If you're unsure when or how a pokémon will evolve, this information is easy to find online. You can check the pokémon's page on a pokémon resource site like bulbapedia , for instance. X research source note that select pokémon will only evolve by using special items or by meeting special conditions. For example, most eevee evolutions require an evolutionary stone to evolve (flareon, vaporeon, leafeon, jolteon) while espeon requires a certain level of friendship to be reached between 6 am-6 pm, and umbreon requires friendship to be reached from 6 pm-6 am. Sylveon requires a soothe bell to be held while it reaches the correct level of friendship, and you must be in the appropriate location for eevee to evolve into glaceon.
War of the AI algorithms: the next evolution of cyber attacks
The history and evolution of cybercrime are easy to track and coincide with the evolution of the internet itself. The first crimes were of course simple hacks to steak information from local networks but as the internet became more established so too did the attacks. While cyber crime existed before this, the first major wave of cyber crime came with the proliferation of email during the late 80’s. It allowed for a host of scams and/or malware to be delivered to your inbox. Remember the nigerian prince scam? “greetings, i am a down-and-out prince from nigeria. I need help getting millions out of my country and all you have to do is send me some money first to set-up the transfer. Once done i’ll share my millions with you†… yeah right.
Chapter 1. Hacker Slang and Hacker Culture
This document is a collection of slang terms used by various subcultures of computer hackers. Though some technical material is included for background and flavor, it is not a technical dictionary; what we describe here is the language hackers use among themselves for fun, social communication, and technical debate. The ‘ cool hacker mugs gift hacker hacker mug culture’ is actually a loosely networked.
The rise of the black hat hacker
As hackers have become smarter and more persistent, it has become increasingly important for companies to have adequate defences against them. This is why we have seen the concept of ethical hacking increasingly used by cybersecurity firms as a way to combat the problem. Ethical hacking is now commonplace – it’s even possible to become what is known as a certified ethical hacker. The practice is also known as white hat hacking, and it involves using the same techniques that black hat hackers use in order to break down cyber defences. The difference is that when a white hat hacker has compromised those defences they inform the business of how they managed to do it so that the vulnerability can be fixed.
The mainstream media 's current usage of the term may be traced back to the early 1980s. When the term was introduced to wider society by the mainstream media in 1983, even those in the computer community referred to computer intrusion as "hacking", although not as the exclusive definition of the word. In reaction to the increasing media use of the term exclusively with the criminal connotation, the computer community began to differentiate their terminology. Alternative terms such as " cracker " were coined in an effort to maintain the distinction between "hackers" within the legitimate programmer community and those performing computer break-ins. Further terms such as " black hat ", " white hat " and " gray hat " developed when laws against breaking into computers came into effect, to distinguish criminal activities from those activities which were legal.
There are three types of hackers: white hat: these hackers search for bugs or weaknesses in large companies, notify their technology or security teams and receive a bounty from the company that ranges in value depending on the threat and weakness. This is how many companies are staying ahead of black hat hackers and cyber criminals.
A Hacker’s Perspective on Cyber Security
Go to the library of all the nova labs videos, including the cybersecurity lab videos: cybersecurity 101, cyber codes, the secret lives of hackers, and a cyber privacy parable.
Beginning in june 2011, hackers from anonymous and lulzsec collaborated on a series of cyber attacks known as "operation antisec". On june 23, in retaliation for the passage of the immigration enforcement bill arizona sb 1070 , lulzsec released a cache of documents from the arizona department of public safety , including the personal information and home addresses of many law enforcement officers. On june 22, lulzsec brazil took down the websites of the government of brazil and the president of brazil. Later data dumps included the names, addresses, phone numbers, internet passwords, and social security numbers of police officers in arizona , missouri , and alabama. Antisec members also stole police officer credit card information to make donations to various causes.
The national cyber security centre (ncsc) has detected a rise in cyber attacks targeting academic institutions, including schools and universities. Read here over the years, hackers have consistently reinforced the old adage: ‘where there’s a will there’s a way’. Defenders have inputted new rules into their firewalls or developed new detection signatures based on attacks they have seen, and hackers have constantly reoriented their attack methodologies to evade them, leaving organisations playing catch-up and scrambling for a plan b in the face of an attack. A paradigm shift came in 2017 when the destructive ransomware ‘worms’ wannacry and notpetya caught the security world unaware, bypassing traditional tools like firewalls to cripple thousands of organisations across 150 countries, including a number of nhs agencies.
Just like cyber security professionals are constantly looking for ways to develop better and more secure software programs, hackers are always staying on top of the newest updates to overcome the latest defenses. To understand the importance of cyber security and how to stay ahead of hackers, it can be helpful to look at things from the opposite point of view—a hacker trying to get into your business’s system.
î ‚november 25, 2020î „the hacker news many of us here would love to turn hacking into a full-time career. To make that dream come true, you need to master your subject and earn some key certifications. To speed up this process, you might want to take a little guidance from the experts. Featuring 98 hours of content from top instructors, the ultimate 2020 white hat hacker certification bundle  is the ultimate launchpad for your career. It provides an incredible introduction to white hat hacking and helps you become a comptia-certified professional. The courses in this bundle are separately worth $1,345, but the hacker news has put together a special deal for readers. Special offer  — for a limited time, you can  pick up all 10 courses for just $39. 90  with this bundle. That's a 97% saving on the full price! according to cybersecurity ventures, there will be 3. 5 million unfilled cybersecurity jobs by next year. If you want to take advantage of this gold rush, now is an excellent time to start studying. Perfect for.
Search
Categories
- Stock Trader
- Criminologist
- Coworker Leaving
- Mortician
- Virologist
- Veterinary Technician
- Title Examiner
- Team Leader
- Technical Recruiter
- Senator
- Scribe
- Perioperative Nurse
- pediatrician
- Modeller
- Military
- Economist
- Coworker
- Captain
- Arborist
- Voter
- 14
- 12
- Worker
- Chemistry
- Actuary
- Actor
- Announcer
- Wellness Nurse
- Judge
- Academic Dean
- Administrator
- Agricultural
- Administrative Assistant
- Agronomist
- Barber
- Analyst
- Pharmacist
- Call Center Support
- Cameraman
- Interventional Radiologist
- Wedding Officiant
- Politics
- Public Health
- Respiratory Therapist
- Singer
- Sniper
- Teacher
- Manatee
- Hacker
- Gambling
- Flight Attendant
- Entertainer
- Employee
- Daily Nutritionist
- Kitchen Manager
- Astronomer
- American Upholsterer
- Activist
- Accountant
- Writer
- Vice President
- Inventor
- Drafter
- Debater
- Carpenter
- Baker
- Attorney
- Astronaut
- Advisor
- Occupational Therapist
- Nutritionist Fact
- Municipal Arborist
- Management
- Mail Carrier
- Livestock Farmer
- Landscape Contractor
- Land Surveyor
- Insurance Investigator
- Insurance Broker
- Inspector
- Hunter
- Historian
- Hiker
- Hairstylist Black
- Hairstylist
- Gunsmith
- Gun Shooter
- Grant Writer
- Government Auditor
- Gold Panning
- Gardener
- Forensic
- Fisherman
- Fireman
- Firefighter
- Esthetician
- Entrepreneur
- Engineer
- EMT
- Electrician
- Driller
- Doctor
- Diver
- Dispatcher
- Dishwasher
- Director
- Dietitian
- Detective
- Dancer
- Creative Writing
- Counselor
- Cloud Architect
- Climber
- Chef
- Chairman
- Cardiac Sonographer
- Boss
- Bookkeeper
- Bee Keeper
- Bartender
- Auctioneer
- Architect
- Appraiser
- Watchmaker
- Wanker
- Typist
- Trooper
- Train Controller
- Tool and Die Maker
- Therapist
- Technician
- Surgeon
- Supervisor
- Stripper
- Soldier
- Sociologist
- Social Worker
- Sheriff
- Sexy Pick Up Lines
- Self Reminder
- Secretary
- Scientist
- Scheduler
- Sailor
- Roofer
- Marshal
- Manager
- Librarian
- Lawyer
- Landscaper
- Investigator
- Retirement
- Registered Nurse
- Recruiter
- Records Clerk
- Realtor
- Rancher
- Quilter
- Psychology
- Psychologist
- Principal
- Priest
- Postmaster
- Office Assistant
- Nutritionist
- Nurse
- Network Administrator
- Mechanic
- Mayor
- Podiatrist
- Plumber
- Planner
- Pipe Fitter
- Pilot
- Photographer
- Phlebotomy Technician
- Painter
- Nurse Practitioner
- Identifier
- Lacemaker
- HRD
- Hatter
- Host
- Herdsman
- Bouldering
- Assassin
- Bomberman
- Army
- Attendant
- Blogger
- Clergyman
- Cashier
- Botanist
- Bodyguard
- Aquascaping
- Assistant
- Electorate
- Physician
- Arbitrator
- Administrative