Game & Hack Information
by Justin
Posted on 30-11-2020 03:22 PM

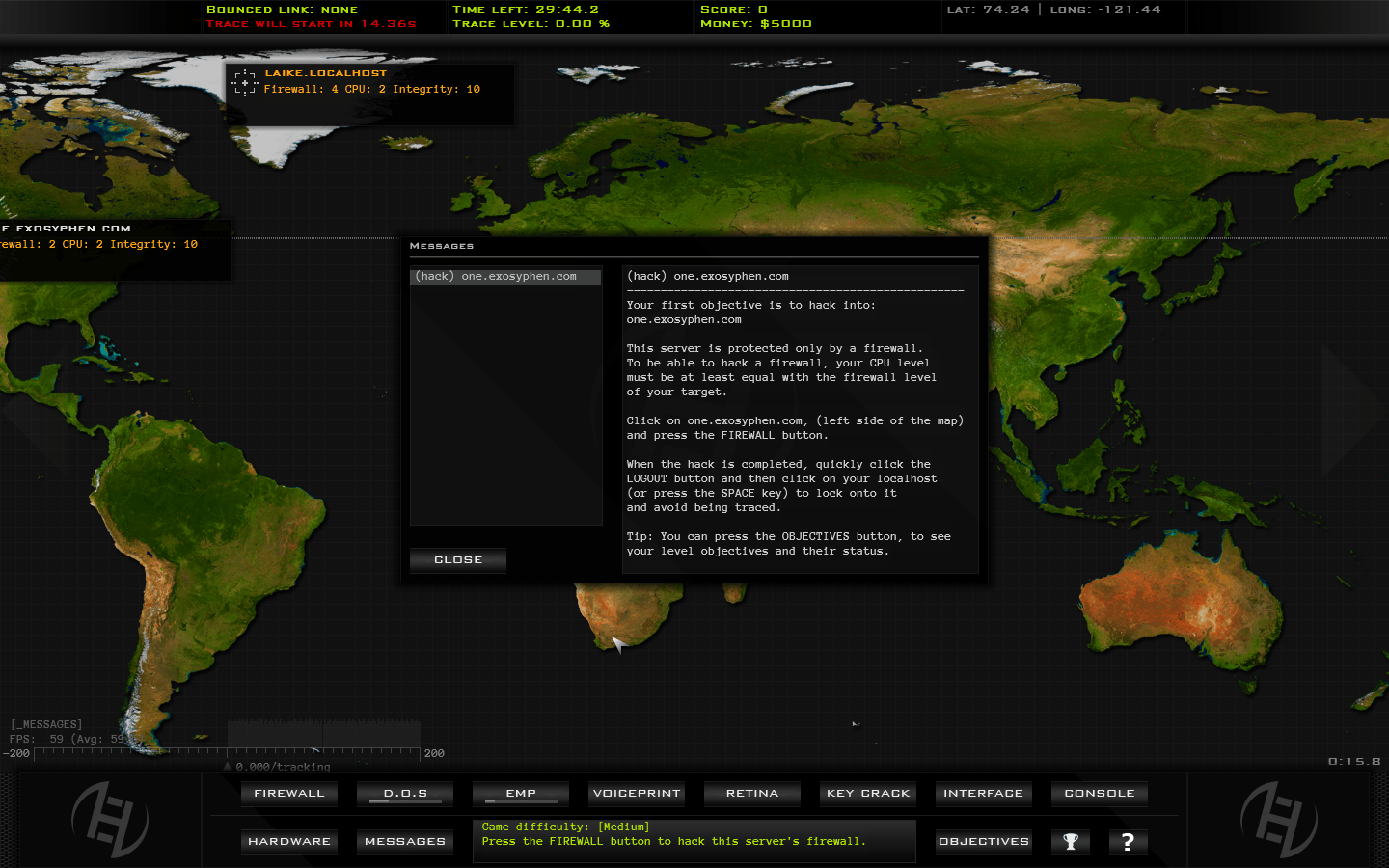
In this game you take on the role of brian spencer, an ex-cia security technologist who must hack into computer networks to uncover the source of recent attacks on major systems across the globe. You hack into computers, look for exploits and information, steal money to buy hardware upgrades in an attempt to put all the pieces of a big puzzle together.

Plot[ edit ] activision executive jim levy introduced hacker to reporters by pretending that something had gone wrong during his attempt to connect on line to company headquarters to demonstrate a new game. After several attempts he logged into a mysterious non-activision computer, before explaining, "that, ladies and gentlemen, is the game". The player assumes the role of a hacker , a person experienced in breaking into secure computer systems, who accidentally acquires access to a non-public system. The game was shipped with no information on how to play, thus building the concept that the player did hack into a system.
Evolution [ edit ]
Hacker evolution
cheat codes:
------------
put this into the regular command prompt of the game. Another way is to puch 'x'
and hit tab to fulfill code. Effect code
-------------------------------------------------------------
xmoney - get $10000.

Open/close dossier for add points/points editor cheats to work. Included in cheat evolution app.
Jurasic world evolution is coming to the nintendo switch with a new complete edition. Check out this gamescom trailer here!.
Changes in Evolution of Species 2:
â–ª transformation
â–ª power cult
explore each branch to open the next. By tapping the last two life forms at this stage, you get access to a new, previously unknown world! discover all the planets in this fun evolution game!
you start in the beginning world with a small lizard. By combining two creatures, you create a new, more perfect being. You don’t need little alchemy or magic to evolve faster.
 Just click on the creatures to earn coins and buy more species to merge. Offline autoclicker included in this the game of life and planet evolution!.
Just click on the creatures to earn coins and buy more species to merge. Offline autoclicker included in this the game of life and planet evolution!.
One of the initial buildings available in jurassic world evolution, the research center is a vital addition to any park, allowing players to progress through a myriad of research trees, thus unlocking new dinosaur species, genetic materials, buildings & upgrades, diseases , operation improvements, and additional dig and research teams. Three upgrade slots can be applied to each research center which allow players to both reduce the cost and the length of research times on all island sites.
Digimon Story: Lost Evolution
⇨ english
生体ã«ã¤ã„ã¦è¬Žã«åŒ…ã¾ã‚ŒãŸä¸æ€è°ãªãƒ‡ã‚¸ãƒ¢ãƒ³ã€‚ã²ã¨ãªã£ã“ãã¦éŠã³ãŒå¤§å¥½ãã§ã€æ¥½ã—ã„ã“ã¨ãŒã‚ã‚‹ã¨ã©ã“ã‹ã‚‰ã‹ã‚„ã£ã¦ãる。ã“ã¨ã°ã®æœ€å¾Œã«ã€Œã‚¯ãƒ«ã€ã‚’ã¤ã‘ã‚‹ã®ãŒå£ã‚°ã‚»ã€‚デジモンã®ãƒ‘ラメータãªã©ã«ã¤ã„ã¦ã‚ˆã知ã£ã¦ã„ã¦ã€ãƒ‡ã‚¸ãƒ©ãƒœã®é€²åŒ–ツリーを管ç†ã—ã¦ã„る。
⇨ japanese
the force governing evolution called "digi-entelechy" that was transformed into a digimon. It is said that it has the power to promote the evolution of other digimon. Digimon story: sunburst & moonlight
⇨ english
「デジ・エンテレケイヤã€ã¨ã€€ã‚ˆã°ã‚Œã‚‹
進化を ã¤ã‹ã•ã©ã‚‹ã€€ã¡ã‹ã‚‰ãŒã€€ãƒ‡ã‚¸ãƒ¢ãƒ³åŒ–ã—ãŸã€€ãã‚“ã–ã„
ã»ã‹ã®ã€€ãƒ‡ã‚¸ãƒ¢ãƒ³ã®ã€€é€²åŒ–ã‚’
ãŸã™ã‘る ã®ã†ã‚Šã‚‡ãを もã¤ã¨ã€€ã„ã‚ã‚Œã¦ã„ã‚‹
デジモンストーリー サンãƒãƒ¼ã‚¹ãƒˆï½œãƒ ーンライト
⇨ japanese
a small digimon that does not evolve or attack, not seeming like a digimon at all. It is rumored to have the ability to help the evolution of other digimon.

How to Hack Evolution
Stock exchanges. Central banks. Satellite uplinks. Transoceanic fiber optics links. All mysteriously succumbing to an unexpected “evolution†of the web. When the world’s critical services start to collapse, you know this is more then a simple event. Who or what is behind it? only an experienced and dedicated hacker, with know-how gained as an international cyber-intelligence agent, can root out the cause and bring it down.
The gaming industry has been growing at a rapid pace. The likes of the players get people to employ various cheats and hack to rise up on the leaderboard faster. The sandbox evolution hack allows you to add unlimited karma to your wallet with ease. Add unlimited amount of karma and use these hacks to get your pro game on! we are going to take you to another new gaming hack, which is easy to use and does not even make you go through endless software installation, which ends up being wary of installing malicious software in your computers or mobile phones. Another issue to tackle being, connectivity. Players usually get disconnected in between the game and that causes chaos. This online hack gives you complete protection from such connectivity issues as well. It is popular among players and doesn’t let your teammates hang out to dry. Such features allow you to rise high and shine and it does not even require you a lot of effort.
Do you want to get unlimited evolution? and if you do, you can use this hack code "ggi-6234cc2c04" if you don't know how to enter cheat codes in deeeep. Io , you will read about it below. If you want to get more deeeep. Io cheats, then share this page in one of the social networks:.
Evolve your pokemon pets to their mega evolution stages in this fun pokemon rom hack for the game boy advance - pokemon omega ruby! pokemon omega ruby is a pokemon rom hack for the game boy advance handheld system (gba). The game is based on pokemon ruby and features the same storyline as the original game. Although it has the same title as the popular nds game, the game was actually not based on it. The main difference of this hack as compared to the original pokemon ruby version is the addition of mega evolution. In this rom hack, there are 22 pokemon that can use the mega evolution that will turn the pokemon into a much more stronger version of itself with even more attack variations.
Much to our surprise, we were able to hack our kryptonite evolution 2000 u- lock with a ballpoint pen. This $50 lock is supposed to be one of the best for "toughest bicycle security in moderate to high crime areas"—unless the thief happens to have a bic pen. We used to use these to lock up our bicycles, but we're switching to something else asap. (oh, and just to be.
Pro Evolution Soccer 2019
14. 310 views pro evolution soccer 2010 (pes 10) pc download full version – sebuah game sepak bola tahun 2010, bisa menjadi media untuk nostalgia, game ini sudah bergrafis mirip dengan ps3, game ini juga lumayan ringan buat dimainkan di pc dan laptop low spec, sebelumnya mimin sudah membagikan link download game sepak bola ringan jadul yaitu pro evolution soccer 2007 pc download.
Get in the game
Always make a backup of the files that are overwritten by the file archive, as the original files are usually required to update the game to a newer version or to play online! some no-cd/fixed exe files work fine in single player mode but are detected to be modified when trying to play online. When this happens use the original exe to play online, else you could find yourself banned from the game!.
Slither. Io hack tool is easy to use and can be used in simple steps. It is definitely not rocket science and nothing in comparison what gamers are subjected to on an everyday basis. There is no installation required for any kind of software on your system. You just need to follow simple steps to get the hack working. Following are the steps that you can use to access the online hack tool:.
Cjs cd keys sell brand new cd keys taken directly from brand new sealed copies of the game. We source our keys in bulk direct from major distributors. After you receive your key, you can activate the game on the steam client (available free from steampowered. Com). After you activate the game with the steam software, you can download the game immediately and instantly.
The game beyblade burst is based on the manga of the same title. This is a story of the visionary future world where people take part in unusual competitions and fight with each other to earn money for the battles. People themselves are just trainers, while the participants are small mechanisms that are carefully assembled, tested, and endowed with various weapons. As one of the participants, you want to win all the battles and become a champion. Your robot will meet numerous rivals on the arena and use his super abilities to prove that he is the strongest one. He will master various fighting styles, moves, and attacks to level up and evolve. There are more than forty characters in the game, including the most popular ones like valt and aiga, so players have an amazing chance to arrange battles they have never seen in manga (but always wanted). The battles in beyblade burst are incredibly dynamic and fierce, so you will have a really good time while you play. The game has a lot of customization options, which allows you to create a bey of your dream and compete with other gamers from all over the world. Whether you want to bring your friends and challenge them for a battle or meet someone online – both these options are available in the game. The application is full-fledged only if you already have beyblade burst products, namely the official toys. The game will request an access to your camera to check the code on your items, so don’t forget to adjust the privacy settings and turn on the camera.
Modding capability to allow the creation of custom levels the included mod editor, allows you to create new game levels easily complex levels and game play to guarantee the best experience complex command console with over 20 commands and tools.
Source: imore gotta catch 'em all… pokémon! since 1995, that's what the pokémon company has told us to do and boy, have we! twenty-five years later, we're still trying to catch them all. Whether you're playing the mobile game pokémon go , pokémon sword and shield on your nintendo switch , or one of the older games, there are nearly 900 different pokémon available and many have multiple forms. Even for the experts, keeping track of all these creatures can be overwhelming. That's where having a complete pokémon pokédex becomes absolutely necessary and now, we have just that for you!.
The visitor is an interactive horror adventure game. Guide an alien parasite through its new earthly surroundings in this adventurous game. The visitor is alien and comes from a strange world. He seems to be harmless and looks like a tiny worm, but he came to conquer the earth. Help him to grow and to become stronger, by eating all living creatures on the planet. Start with the small ones, like insects, birds or fish. Click on the different items in the picture and solve all puzzles to feed this hungry monster.
The History Of Computer Hacking And How It Has Evolved Over The Years
/in history of technology /by pro oncall technologies the 1983 movie wargames gave us insight to the world of computer hacking as matthew broderick almost started world war iii because of his desire to play a new video game. While hacking was once synonymous with nerdy teenagers, large companies like target and sony pictures will argue that it has come much farther than that. Major cyber crimes are being committed and breaches in online security are becoming more commonplace. Criminals are so smart that they can decrypt personal data and destroy people’s identity with the design of malicious software. To understand how this happened, let’s take a look at how computer hacking has evolved over the years.
The History of Computer Hacking
Cyber warfare seems to be dominating headlines as of late. Be it a clandestine groups hacking computers for ‘fun’ or alleged government agencies attempting to steal classified information, the internet landscape has been transformed into a binary battlefield. Who needs a gun when you have a keyboard? with many of us unlikely to join in on the action, arn has assembled a list the most notorious cyber attacks in history.
The History of Hacking - The First Hackers
Posted by: admin if you think hackers get a bad rap, think about this…… the word “hacking†has become synonymous with ill doings and the amount of affected people might be the reason for that. The meanings of hacking are many and most are intended to describe the act of engaging in activities (such as programming or other media) in a spirit of playfulness and exploration. But, the destructive intentions of some hackers have turned this word into something bad. For a better understanding, let’s have a look at the hacking history timeline.
though ransomware has been around for years, it poses an ever-increasing threat to hospitals , municipal governments , and basically any institution that can't tolerate downtime. But along with the various types of pc malware that are typically used in these attacks, there's another burgeoning platform for ransomware as well: android phones. And new research from microsoft shows that criminal hackers are investing time and resources in refining their mobile ransomware tools—a sign that their attacks are generating payouts.
Search
Categories
- Stock Trader
- Criminologist
- Coworker Leaving
- Mortician
- Virologist
- Veterinary Technician
- Title Examiner
- Team Leader
- Technical Recruiter
- Senator
- Scribe
- Perioperative Nurse
- pediatrician
- Modeller
- Military
- Economist
- Coworker
- Captain
- Arborist
- Voter
- 14
- 12
- Worker
- Chemistry
- Actuary
- Actor
- Announcer
- Wellness Nurse
- Judge
- Academic Dean
- Administrator
- Agricultural
- Administrative Assistant
- Agronomist
- Barber
- Analyst
- Pharmacist
- Call Center Support
- Cameraman
- Interventional Radiologist
- Wedding Officiant
- Politics
- Public Health
- Respiratory Therapist
- Singer
- Sniper
- Teacher
- Manatee
- Hacker
- Gambling
- Flight Attendant
- Entertainer
- Employee
- Daily Nutritionist
- Kitchen Manager
- Astronomer
- American Upholsterer
- Activist
- Accountant
- Writer
- Vice President
- Inventor
- Drafter
- Debater
- Carpenter
- Baker
- Attorney
- Astronaut
- Advisor
- Occupational Therapist
- Nutritionist Fact
- Municipal Arborist
- Management
- Mail Carrier
- Livestock Farmer
- Landscape Contractor
- Land Surveyor
- Insurance Investigator
- Insurance Broker
- Inspector
- Hunter
- Historian
- Hiker
- Hairstylist Black
- Hairstylist
- Gunsmith
- Gun Shooter
- Grant Writer
- Government Auditor
- Gold Panning
- Gardener
- Forensic
- Fisherman
- Fireman
- Firefighter
- Esthetician
- Entrepreneur
- Engineer
- EMT
- Electrician
- Driller
- Doctor
- Diver
- Dispatcher
- Dishwasher
- Director
- Dietitian
- Detective
- Dancer
- Creative Writing
- Counselor
- Cloud Architect
- Climber
- Chef
- Chairman
- Cardiac Sonographer
- Boss
- Bookkeeper
- Bee Keeper
- Bartender
- Auctioneer
- Architect
- Appraiser
- Watchmaker
- Wanker
- Typist
- Trooper
- Train Controller
- Tool and Die Maker
- Therapist
- Technician
- Surgeon
- Supervisor
- Stripper
- Soldier
- Sociologist
- Social Worker
- Sheriff
- Sexy Pick Up Lines
- Self Reminder
- Secretary
- Scientist
- Scheduler
- Sailor
- Roofer
- Marshal
- Manager
- Librarian
- Lawyer
- Landscaper
- Investigator
- Retirement
- Registered Nurse
- Recruiter
- Records Clerk
- Realtor
- Rancher
- Quilter
- Psychology
- Psychologist
- Principal
- Priest
- Postmaster
- Office Assistant
- Nutritionist
- Nurse
- Network Administrator
- Mechanic
- Mayor
- Podiatrist
- Plumber
- Planner
- Pipe Fitter
- Pilot
- Photographer
- Phlebotomy Technician
- Painter
- Nurse Practitioner
- Identifier
- Lacemaker
- HRD
- Hatter
- Host
- Herdsman
- Bouldering
- Assassin
- Bomberman
- Army
- Attendant
- Blogger
- Clergyman
- Cashier
- Botanist
- Bodyguard
- Aquascaping
- Assistant
- Electorate
- Physician
- Arbitrator
- Administrative