Are you a hacker?
by Justin
Posted on 30-11-2020 03:21 PM

From the developer:
from the creators of a successful hacker games series (digital hazard, bs best hacker gifts gift for hacker hacker gifts ideas , etc) hacker evolution is a new hacking simulation game, featuring unparalleled graphics and features. You play the role of a former intelligence agent, specializing in computer security. When a chain of events sets off worldwide, leaving critical service disabled, you assume the role a computer hacker to find out what happened and attempt to stop it.
‘not v interesting†is thom yorke’s assessment of the 16-odd hours of unheard radiohead music, recorded between 1995 and 1998, that the band have just shared online. Jonny greenwood was marginally more effusive: “only tangentially interesting. And very very long. †you get the sense that their hand was forced by a hacker who was hoping to charge $150,000 for the recordings, which were subsequently leaked; the band are now selling them and giving the proceeds to environmental campaigners extinction rebellion.
Nowadays, the word “hacker†carries an overwhelmingly negative connotation, conjuring up images of digital thieves intent on stealing identities and letting disruptive viruses loose into cyberspace. It wasn’t always that way. In fact, computer hackers were originally viewed by society as technology enthusiasts who wanted nothing more than to optimize, customize and tinker. It wasn’t until decades later – with the birth of viruses and cyber crime – that traditional hackers got lumped together with those of malicious intent and the public vilification of hacking began.
Hacker evolution guides zer0's guides this item has been removed from the community because it violates steam community & content guidelines. It is only visible to you. If you believe your item has been removed by mistake, please contact steam support. This item is incompatible with hacker evolution. Please see the instructions page for reasons why this item might not work within hacker evolution.
î ‚november 19, 2020î „ the hacker news emotet is one of the most dangerous and widespread malware threats active today. Ever since its discovery in 2014—when emotet was a standard credential stealer and banking trojan, the malware has evolved into a modular, polymorphic platform for distributing other kinds of computer viruses. Being constantly under development, emotet updates itself regularly to improve stealthiness, persistence, and add new spying capabilities.
Short bytes: using simple hacks, a hacker can know about your personal unauthorized information which you might not want to reveal. Knowing about these common hacking techniques like phishing, ddos, clickjacking, etc. , could come handy for your personal safety. Unethical hacking is an illegal activity of accessing unauthorized information by modifying a system’s features and exploiting its loopholes. In this world where most of the things happen online, hacking provides wider opportunities for hackers to gain unauthorized access to the unclassified information like credit card details, email account details, and other personal information.
Persistence is what a hacker needs to make it to their goal. That’s exactly what it took for [erik] to make an untethered vr backpack system. Starting way back in the spring of 2019, [erik] began working on an untethered vr system. Sure, the oculus quest was coming out, but it wouldn’t be compatible with the game library of pc based systems. [erik] decided he wanted the best of both worlds, so he decided to build a backpack that carries a computer powerful enough to drive the rift s.
Top Games Right Now
What does this mean for me? you will always be able to play your favorite games on kongregate. However, certain site features may suddenly stop working and leave you with a severely degraded experience.
 What should i do? we strongly urge all our users to upgrade to modern browsers for a better experience and improved security.
What should i do? we strongly urge all our users to upgrade to modern browsers for a better experience and improved security.
Hungry shark evolution desktop is a well-assembled hybrid of side-scrollers, simulators, and casual games. Let us walk you through these genres one-by-one.
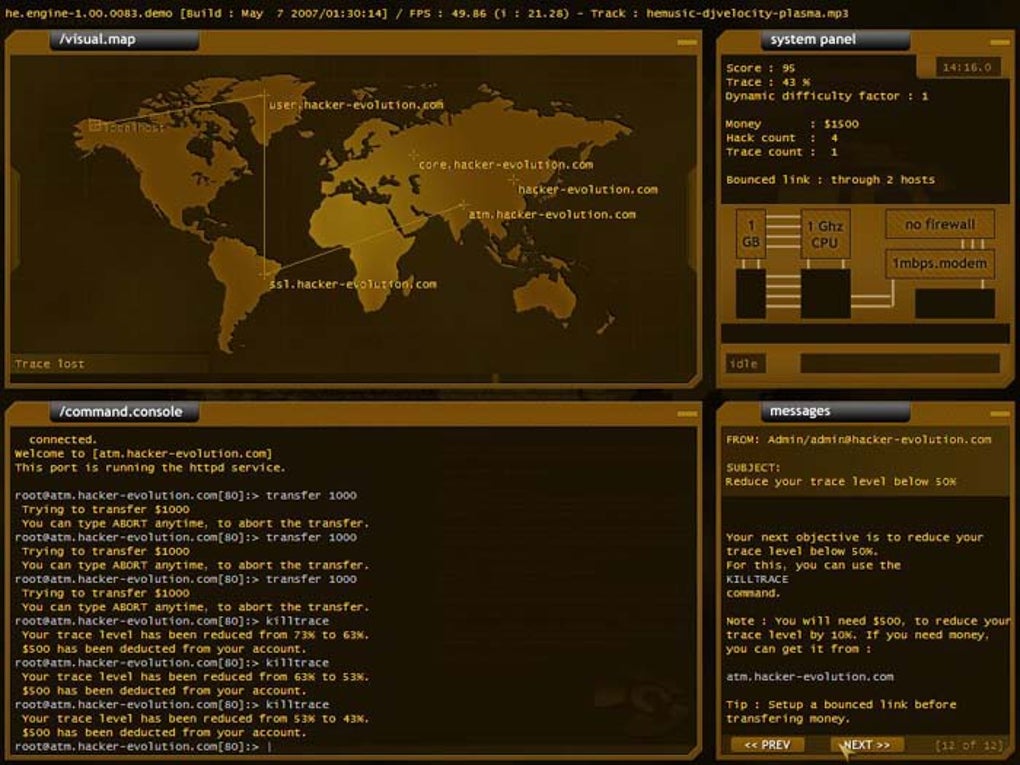
Hacker Evolution – Guide and Walkthrough
Updated: 05/28/2007
unofficial strategy guide and faq
by kasey chang
released may 22, 2007
1 introduction
this section is for "what the faq is about" and things like that. Feel free to skip this section. If you like the faq, please send me a dollar. :-) see [1. 3]
this faq is about "hacker evolution", a "hacking simulation".

Games You May Like
June 18, 2019 - rail adventures beta available for free download + steam early access purchase option head over to the rail adventures page to download a free beta or purchase a steam copy of the game. June 15, 2019 - new website available with updated information on our games dear gamers, we have taken some time of to rest and organize certain things around here.
Before i start the tutorial and show you multiple ways to hack hungry shark world game on iphone, i want to let you know that hacking games is not recommended cause of a couple of reasons. Developers of apps and games rely on the revenue coming from in app purchases and they deserve each bit of that revenue.
This page will show the changes made by the "change impossible evo[lution]s" option in the latest randomizer. Check here to see how to evolve your pokemon after using this option. The lists are separated by the games they are used in. In some cases this only changes by generation, in others there will be smaller changes inside the same generation (such as some games not having contests etc).
Level up with the best games for windows, mac, android, and ios. Find a puzzle game you can drop right into, escapist rpgs, or intense strategy games. Get our tips on what's good, what's free, and what's worth paying for.
Having only barely known about "hacking" games, i decided to give it a shot, as this game was on sale for 2€. I found myself having mixedhaving only barely known about "hacking" games, i decided to give it a shot, as this game was on sale for 2€. I found myself having mixed feelings about it, and writing a lot, so bear it with me. (skip to the last paragraph, above the ps, if in a hurry).
You are about to experience another new pokemon firered game, pokemon dark rising 2 is based from pokemon firered. What’s the special with most of modified and improved pokemon games especially dark rising 2 is that you can meet and catch pokemon which are not available in the original firered game.
The sb game hacker application is an application that is able to run along side a multitude of games. This application must be open while a game is open at the same time too. This allows players to alter values within games such as the attack points for certain weapons, the time clock in games, as well as the speed of the character.
The Evolution of Hacking
Hacker evolution: immersion hacker evolution duality hacker evolution duality is a hacking simulation game, developed by exosyphen studios. Based on the successful hacker realpolitiks ii anno 2070 developed by related designs in collaboration with blue byte, anno 2070 takes place in a near-future environment wher crusader kings iii.
This the sandbox evolution patch is created by russian programmers so that everyone could get everything in the game for free. There are two versions of the patch - one for ios, and the other for android. So if you using android device, then you need to download a patch for the android, and if the ios device, then download ios version of patch. Otherwise you just can't launch this hacking on your device.
C|eh (master) is the world’s first performance-based ethical hacking industry readiness certification, that is verified, online, live, and proctored. C|eh master is the next evolution for the world-renowned certified ethical hacker credential and a logical ‘next step’ for those holding the prestigious certification. Earning the c|eh master designation is your way of saying, “i learned it, i understood it, and i proved it. â€.
The fast evolution and constant threat of cyber attacks, our ever-growing reliance upon digital processes, and the exponential increase in online data makes cyber security one of the greatest challenges of our time. Despite this, few are equipped with the necessary skills to tackle it. Hacker house was created to close the skills gap quickly, efficiently and effectively. Taught by world-renowned ethical hackers, our students are plunged head-first into real world cyber-attack simulations and are assessed across a variety of practical assignments designed to cover every angle. In short, we teach students how to think, act and move like a hacker – and then outmanoeuvre them. We provide technical resources to assist companies in understanding the complex cyber threat theatre. From computer hacking, electronic surveillance, counter measures, espionage, exploits and malicious code.
Evolution of Emotet: From Banking Trojan to Malware Distributor
Hkcert security newsletter (november 2020 issue) 2020/11/02 identity theft protection for social media and instant messaging accounts 2020/10/28 interpol arrests 3 nigerian bec scammers for targeting over 500,000 entities [the hacker news] 2020/11/26 evolution of emotet: from banking trojan to malware distributor [the hacker news] 2020/11/24 facebook messenger bug lets hackers listen to you before you pick up the call [the hacker news].
Gameplay (4 out of 5)
The award winning series returns taking the famed gameplay to a new level by achieving interactive reality in both control and new authentic visuals. Control reality in pro evolution soccer 2017 with these new features: real touch – players control the ball in unique ways based on where and how you control them.
This game is offering some of the best graphics as well as features. Even you can get amazing gameplay, but due to large size, there is a need for better configuration. To run jurassic world evolution crack, the system requirement is – * processor: intel core i5-2300 * system requirement: microsoft windows 7.
Need help with this game? Please visit our Flash page.
Share you own hack tricks, advices and fixes. Write review for each tested game or app. Great mobility, fast server and no viruses. Each user like you can easily improve this page and make it more friendly for other visitors. Leave small help for rest of app' users. Go ahead and simply share funny tricks,.
Dragon Ball Z Devolution
Pokemon radical red v2. 1pokemon eclat pourpre 2. 5 spanish version pokemon sienna final version dragon ball z team training v8 pokemon sword & shield beta 8 pokemon nameless v3. 53 pokemon let's go pikachu gba v5. 0. 0pokemon unbound battle tower 1. 4. 5. 1pokemon gs chronicles 2. 5pokemon adventure red chapter b15+ex pass.
Pathogenicity islands and the evolution of microbes
Virulence factors of pathogenic bacteria (adhesins, toxins, invasins, protein secretion systems, iron uptake systems, and others) may be encoded by particular regions of the prokaryotic genome termed pathogenicity islands. Pathogenicity islands were first described in human pathogens of the species escherichia coli, but have recently been found in the genomes of various pathogens of humans, animals, and plants. Pathogenicity islands comprise large genomic regions [10-200 kilobases (kb) in size] that are present on the genomes of pathogenic strains but absent from the genomes of nonpathogenic members of the same or related species. The finding that the g+c content of pathogenicity islands often differs from that of the rest of the genome, the presence of direct repeats at their ends, the association of pathogenicity islands with transfer rna genes, the presence of integrase determinants and other mobility loci, and their genetic instability argue for the generation of pathogenicity islands by horizontal gene transfer, a process that is well known to contribute to microbial evolution. In this article we review these and other aspects of pathogenicity islands and discuss the concept that they represent a subclass of genomic islands. Genomic islands are present in the majority of genomes of pathogenic as well as nonpathogenic bacteria and may encode accessory functions which have been previously spread among bacterial populations.
In february 2009, someone hacked kvoa in tuscon, arizona, during a live transmission of the super bowl xliii between the arizona cardinals and the pittsburgh steelers. The hack only affected viewers in tucson who were watching the game on kvoa through comcast. The hacker replaced the game with 30 seconds of pornography featuring a couple engaged in what viewers called “a graphic act. †interestingly, many people watching thought it was just another commercial until the couple, shall we say, went overboard. The video itself was from club jenna, an adult cable television channel.
Search
Categories
- Stock Trader
- Criminologist
- Coworker Leaving
- Mortician
- Virologist
- Veterinary Technician
- Title Examiner
- Team Leader
- Technical Recruiter
- Senator
- Scribe
- Perioperative Nurse
- pediatrician
- Modeller
- Military
- Economist
- Coworker
- Captain
- Arborist
- Voter
- 14
- 12
- Worker
- Chemistry
- Actuary
- Actor
- Announcer
- Wellness Nurse
- Judge
- Academic Dean
- Administrator
- Agricultural
- Administrative Assistant
- Agronomist
- Barber
- Analyst
- Pharmacist
- Call Center Support
- Cameraman
- Interventional Radiologist
- Wedding Officiant
- Politics
- Public Health
- Respiratory Therapist
- Singer
- Sniper
- Teacher
- Manatee
- Hacker
- Gambling
- Flight Attendant
- Entertainer
- Employee
- Daily Nutritionist
- Kitchen Manager
- Astronomer
- American Upholsterer
- Activist
- Accountant
- Writer
- Vice President
- Inventor
- Drafter
- Debater
- Carpenter
- Baker
- Attorney
- Astronaut
- Advisor
- Occupational Therapist
- Nutritionist Fact
- Municipal Arborist
- Management
- Mail Carrier
- Livestock Farmer
- Landscape Contractor
- Land Surveyor
- Insurance Investigator
- Insurance Broker
- Inspector
- Hunter
- Historian
- Hiker
- Hairstylist Black
- Hairstylist
- Gunsmith
- Gun Shooter
- Grant Writer
- Government Auditor
- Gold Panning
- Gardener
- Forensic
- Fisherman
- Fireman
- Firefighter
- Esthetician
- Entrepreneur
- Engineer
- EMT
- Electrician
- Driller
- Doctor
- Diver
- Dispatcher
- Dishwasher
- Director
- Dietitian
- Detective
- Dancer
- Creative Writing
- Counselor
- Cloud Architect
- Climber
- Chef
- Chairman
- Cardiac Sonographer
- Boss
- Bookkeeper
- Bee Keeper
- Bartender
- Auctioneer
- Architect
- Appraiser
- Watchmaker
- Wanker
- Typist
- Trooper
- Train Controller
- Tool and Die Maker
- Therapist
- Technician
- Surgeon
- Supervisor
- Stripper
- Soldier
- Sociologist
- Social Worker
- Sheriff
- Sexy Pick Up Lines
- Self Reminder
- Secretary
- Scientist
- Scheduler
- Sailor
- Roofer
- Marshal
- Manager
- Librarian
- Lawyer
- Landscaper
- Investigator
- Retirement
- Registered Nurse
- Recruiter
- Records Clerk
- Realtor
- Rancher
- Quilter
- Psychology
- Psychologist
- Principal
- Priest
- Postmaster
- Office Assistant
- Nutritionist
- Nurse
- Network Administrator
- Mechanic
- Mayor
- Podiatrist
- Plumber
- Planner
- Pipe Fitter
- Pilot
- Photographer
- Phlebotomy Technician
- Painter
- Nurse Practitioner
- Identifier
- Lacemaker
- HRD
- Hatter
- Host
- Herdsman
- Bouldering
- Assassin
- Bomberman
- Army
- Attendant
- Blogger
- Clergyman
- Cashier
- Botanist
- Bodyguard
- Aquascaping
- Assistant
- Electorate
- Physician
- Arbitrator
- Administrative