What is Forensic Analysis?
by Samantha
Posted on 23-10-2020 05:32 AM

Network forensics : the capture, recording, and analysis of network events in order to discover the source of security attacks or other problem incidents.

The study of human remains and mortuary practices is a subcategory of archaeology known as bioarchaeology. This is extremely important in most forensic gift forensic science related gifts forensic science gift gift forensic science related gifts forensic science gift archaeology cases, since human bones are often found. Bones can indicated many characteristics of an individual, which may help to identify who the person was or how they died. The pelvis and skull can give sex of the person. Age can be found by studying bone fusion, tooth formation, eruption, decay, and loss. Bone can also show a broken, then healed bone. So if you know that the suspected victim broke their arm 15 years ago and that bone is indeed healed, it may indicated that is the correct person's body. Bones can also be studied for paleopathology, or the study of bones to determine disease or stress on the body. Through paleopathology, gift for trace forensic scientst science forensic investigation gifts gifts for forensic science archaeologists can determine whether someone did a lot of physical labor, had arthritis, had an iron deficiency, or was malnourished. Certain bones are good predictors of a person's height. One of the most important and more recently available techniques in bioarchaeology is dna analysis. Sometimes dna can be extracted from the bones, which is a definite way to determine the identity of the body.
"the pioneer of forensic linguistics is widely considered to be roger shuy, a retired georgetown university professor and the author of such fundamental textbooks as [creating] language crimes. The field’s more recent origins might be traced to an airplane flight in 1979, when shuy found himself talking to the lawyer sitting next to him. By the end of the flight, shuy had a recommendation as an expert witness in his first murder case. Since then, he’s been involved in numerous cases in which forensic analysis revealed how meaning had been distorted by the process of writing or recording. In recent years, following shuy’s lead, a growing number of linguists have applied their techniques in regular criminal cases. ".
Dna analysis: dennis rader's daughter offered up a dna swab when she suspected her father had something to do with it. The dna was a close match the semen found at the crime scenes. They had to call in a forensic serologist to collect the dna and to process it and match it.
: the application of scientific principles and techniques to matters of criminal justice especially as relating to the collection, examination, and analysis of physical evidence : forensics.
Guo,hong. Jin,bo. Qian, wei. 2013. [online]. Analysis of email header for forensics purpose. Available from: https://ieeexplore. Ieee. Org/document/6524415?fbclid=iwar2g2rrl_55d1d9n47degryz6ajixmfq7ec1hcivei_-vgji2dmsjhmzau8. [accessed:02/14/2019] banday. M. T. 2011. [online]. Techniques and tools for forensic investigation of email. Available from: https://pdfs. Semanticscholar. Org/8625/a3b17d199e5cabbb796bad0df56a7979c77c. Pdf. [accessed:02/14/2019] iyer. R. P, et la. 2017. Email spoofing detection using volatile memory forensics. [online]. Available from: https://ieeexplore. Ieee. Org/document/8228692. [accessed:02/14/2019] virustotal. 2019. [online]. Available from: https://www. Virustotal. Com/. [accessed:02/14/2019].
Computer forensics is the application of investigation and analysis techniques to gather and preserve evidence from a particular computing device in a way that is suitable for presentation in a court of law. The goal of computer forensics is to perform a structured investigation while maintaining a documented chain of evidence to find out exactly what happened on a computing device and who was responsible for it.
Types of Computer Forensic Tools
Anti-forensic techniques can make a computer investigator’s life difficult. From committing fraud in an organization to stealing crucial data, cybercriminals can perform a wide range of nefarious activities. In some cases, these perpetrators try to cover their tracks by deleting browser history, cache memory, and even cookies. But with an upward trend , it is now much convenient for cyber attackers to use already programmed software and tools to alter their digital footprints. Technically, these tools are designed to hide, remove, and eventually hinder cyber forensic analysis. With the use of anti-forensic techniques, it becomes exhausting to retrieve evidence during a computer investigation.

Forensic specialists investigating computer crimes require a set of dedicated tools as well as the use of very specific techniques. Depending on the type of computer device and the kind of digital evidence, investigators may choose one tool or another. A common misconception in the use of computer forensic tools is the belief these tools are only used to solve cyber-crime. While cyber-crime is quickly reaching levels unimaginable just a decade ago, computer forensics is not limited to this kind of crime. In fact, only a small proportion of cases solved by computer forensic specialists is related to cyber-crime.
There are various advantages of forensics. It has a broad spectrum of applications which are very useful to us. Some of the advantages of this science are discussed below. ☛ with the help of certain computer tools, it is possible to control cyber crime. This is done through packet sniffing (sensing critical information in the data packets), ip address tracing (to get the address from where the criminal was accessing), email address tracing (to get the details of the email server and in cases of email bombs). This is called computer forensics.
Forensic software tools are continually developing new techniques for the extraction of data from several cellular devices. The two most common techniques are physical and logical extraction. Physical extraction is done through jtag or cable connection, whereas logical extraction occurs via bluetooth, infrared, or cable connection. There are various types of tools available for mobile forensic purposes. They can be categorized as open source, commercial, and non-forensic tools. Both non-forensic and forensic tools frequently use the same techniques and protocols to interact with a mobile device.
What is a forensic investigation?
Dna is present in most cells of our body. It is unique to each of us, and we leave a trail of it everywhere we go. Forensic investigators take advantage of this, using our dna to draw conclusions about where we’ve been and who we’ve interacted with. Dna analysis has revolutionised forensic science. However, forensic experts have raised concerns that how dna can be used in criminal investigations and in court is often misunderstood and misrepresented.
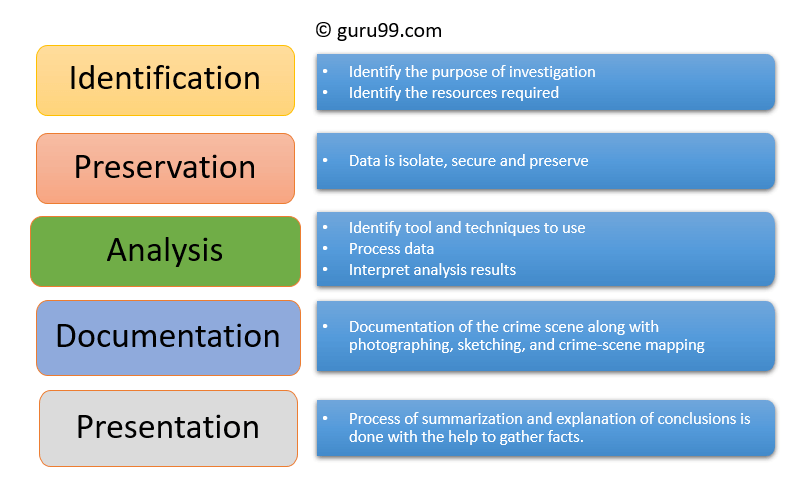
Forensic investigation of emails refers to deeply study the source and content residing in the emails. The study involves identification of the actual sender and recipient of the concerned emails, timestamp of the email transmission, intention of mail, record of the complete email transaction. Investigation of emails proves to be utile in incidents such as email abusing, email phishing, email scams and such other cases where email usage is defamed. Parts of email investigation includes keyword search, metadata investigation, scanning of port, etc.
Forensic mental health may also allow some therapists to profile suspects. For example, they may write or study teachings on the types of people most likely to be serial killers or to commit rapes. In some cases, such profiling also will mean expert testimony, but in many cases, the person simply helps assist in police investigations of specific types of crimes.
Home » crime library » forensic investigation ».
Evidence of violent crimes often includes blood spatters or blood stains. Crime scene investigators will pay close attention to the pattern of blood spatter to try to reconstruct events that took place during the crime. Certain weapons will create distinctive spatter patterns that may be crucial to the investigation. Interpreting a blood stain or spatter is a technique that is often performed by a forensic scientist who specializes in blood analysis.
The increased use of electronic devices and their various features has been a factor in the development of the technical profile of a digital forensics analyst, a role responsible for ensuring certainty in the use of digital images intended to be used as evidence in legal investigations. “the forensic analysis of digital images has become more significant in determining the origin and authenticity of a photograph. â€.
Currently, cybercrime is an increasing danger. Cybercriminals spoof email messages to accomplish illegal activities via email system and remain silent to save themselves during an email forensics investigation. The illegitimate activities include: abuses like spamming, phishing, cyberbullying, child pornography, racial vilification etc. Misuse by transmission of virus, worms, trojan horses, and other malicious programs with an intent to spread them over the internet etc.
Do I need a forensic investigator?
Forensic evaluation is an important component in the work of the forensic psychologist , usually working as part of a team of investigators gathering and evaluating evidence before submitting it to the legal process.

Dear readers, proudly we want to present you the newest issue of eforensics magazine with the focus on anti forensics techniques, detection and countermeasures. Anti forensics techniques are what frustrate the most forensics investigators. Tools used by cybercriminals are becoming more and more sophisticated. How the new obstacles look alike? how to detect and how to work against them? all the answers and more you will find in the newest issue. Do not let yourself to be defeated by hackers. Brace yourself.
Most governments legally recognize the role of forensics in law. When forensic specialists use proven scientific methods in their work, they leave no room for bias. Not only does the field provide detailed examinations and evidence for cases, but it also provides a platform that discourages injustice on the part of investigators. Because of this, dna profiling and other forms of forensic evidence find acceptance in courts around the world.
Forensic science technicians must travel to different locations around a city or region because crimes can occur anywhere. Crime scene investigation can be distressing and unpleasant because investigators see many disturbing sights. Crime scene investigators work staggered day, evening, or night shifts and may have to work overtime because they must always be available to collect evidence.
What is forensic evidence?
→ lawyers applying their forensic skills to every comma of garzon's dossier forensic expert expert (e) médico-légal (e) → forensic experts searched the area for clues → they have called in forensic experts who have identified the bones n preuves fpl relevées lors d'une expertise médicolégale to be convicted on forensic evidence être reconnu coupable sur la base du rapport médico-légal.
Categories biometric r&d | biometrics news | features and interviews | fingerprint recognition (kelvin probe in action. Source: kp technology) forensic technology for fingerprint biometrics used by law enforcement still looks quite similar to what was used generations ago, before computing and digital imaging technology overhauled most of the field of biometrics. Now, a new fingerprint image capturing technique that relies on kelvin probe technology and preserves the evidence for other investigative techniques has been developed.
The fbi provides a variety of forensic services and capabilities, including crime scene documentation; evidence and hazardous evidence….
1 review written by the nation's foremost authority on gunshot wounds and forensic techniques as they relate to firearm injuries, gunshot wounds: practical aspects of firearms, ballistics, and forensic techniques, second edition provides critical information on gunshot wounds and the weapons and ammunition used to inflict them. The book describes practical aspects of ballistics, wound ballistics, and the classification of various wounds caused by handguns, bang guns, rifles, and shotguns. The final chapters explain autopsy technique and procedure and laboratory analysis relating to weapons and gunshot evidence.
This chapter first covers traditional computer forensic incident handling and then converts these tasks and processes to the context of oracle databases, applied to the attacks which have been covered in previous sections. Computer forensics is mainly about dealing with digital evidence within a legally applicable framework. Of interest is that fact that most.
Computer forensics (also known as computer forensic science ) is a branch of digital forensic science pertaining to evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts and opinions about the digital information.
What is forensic science?
Could household slime become a tool to help solve crimes? that's the question u of t mississauga forensic science graduate leanne byrne (h. Bsc, 2020) sought to answer in a recent study that tested a popular children's "slime" recipe as a technique to enhance the appearance of hard-to-see fingerprints in forensic investigations.
What Does Forensic Mean?
Listen: uk:*uk and possibly other pronunciationsuk and possibly other pronunciations/fəˈrÉ›nsɪk/us:usa pronunciation: ipa and respellingusa pronuncation: ipa/fəˈrÉ›nsɪk, -zɪk/ ,usa pronunciation: respelling(fÉ™ ren′sik) ⓘ Îνα ή πεÏισσότεÏα θÎματα συζήτησης στο φόÏουμ είναι ακÏιβώς ίδια με τον ÏŒÏο που αναζήτησατε κÏÏιες μεταφÏάσεις αγγλικά ελληνικά forensic adjadjective: describes a noun or pronoun--for example, "a tall girl," "an interesting book," "a big house. ".
Participants enrolling in this course must meet one of the following employment statuses: licensed or certified peace officer with a current commission employed by or attached to a law enforcement/investigative agency civilian employed by a law enforcement/investigative agency conducting investigative tasks or duties nurse employed by a medical facility tasked with conducting forensic examinations.
Joseph bucklin society. References in brackets [ ] or in curly brackets { } on any page in this website are to books, or other materials, listed in the joseph
does your profile stand out? improve your visibility to members of the legal community who are seeking experts by making these easy and effective enhancements to your online presence. Enhance profile the forensic expert witness association (fewa) is the leading organization for expert witnesses to acquire training, eminence, and certification. Fewa is dedicated to the professional development, ethical standards, and promotion of forensic consultants in all fields of discipline. Fewa stands alone with a combination of benefits for its members, by incorporating networking, education and referrals each as integral aspects of fewa membership.
Search
Categories
- Stock Trader
- Criminologist
- Coworker Leaving
- Mortician
- Virologist
- Veterinary Technician
- Title Examiner
- Team Leader
- Technical Recruiter
- Senator
- Scribe
- Perioperative Nurse
- pediatrician
- Modeller
- Military
- Economist
- Coworker
- Captain
- Arborist
- Voter
- 14
- 12
- Worker
- Chemistry
- Actuary
- Actor
- Announcer
- Wellness Nurse
- Judge
- Academic Dean
- Administrator
- Agricultural
- Administrative Assistant
- Agronomist
- Barber
- Analyst
- Pharmacist
- Call Center Support
- Cameraman
- Interventional Radiologist
- Wedding Officiant
- Politics
- Public Health
- Respiratory Therapist
- Singer
- Sniper
- Teacher
- Manatee
- Hacker
- Gambling
- Flight Attendant
- Entertainer
- Employee
- Daily Nutritionist
- Kitchen Manager
- Astronomer
- American Upholsterer
- Activist
- Accountant
- Writer
- Vice President
- Inventor
- Drafter
- Debater
- Carpenter
- Baker
- Attorney
- Astronaut
- Advisor
- Occupational Therapist
- Nutritionist Fact
- Municipal Arborist
- Management
- Mail Carrier
- Livestock Farmer
- Landscape Contractor
- Land Surveyor
- Insurance Investigator
- Insurance Broker
- Inspector
- Hunter
- Historian
- Hiker
- Hairstylist Black
- Hairstylist
- Gunsmith
- Gun Shooter
- Grant Writer
- Government Auditor
- Gold Panning
- Gardener
- Forensic
- Fisherman
- Fireman
- Firefighter
- Esthetician
- Entrepreneur
- Engineer
- EMT
- Electrician
- Driller
- Doctor
- Diver
- Dispatcher
- Dishwasher
- Director
- Dietitian
- Detective
- Dancer
- Creative Writing
- Counselor
- Cloud Architect
- Climber
- Chef
- Chairman
- Cardiac Sonographer
- Boss
- Bookkeeper
- Bee Keeper
- Bartender
- Auctioneer
- Architect
- Appraiser
- Watchmaker
- Wanker
- Typist
- Trooper
- Train Controller
- Tool and Die Maker
- Therapist
- Technician
- Surgeon
- Supervisor
- Stripper
- Soldier
- Sociologist
- Social Worker
- Sheriff
- Sexy Pick Up Lines
- Self Reminder
- Secretary
- Scientist
- Scheduler
- Sailor
- Roofer
- Marshal
- Manager
- Librarian
- Lawyer
- Landscaper
- Investigator
- Retirement
- Registered Nurse
- Recruiter
- Records Clerk
- Realtor
- Rancher
- Quilter
- Psychology
- Psychologist
- Principal
- Priest
- Postmaster
- Office Assistant
- Nutritionist
- Nurse
- Network Administrator
- Mechanic
- Mayor
- Podiatrist
- Plumber
- Planner
- Pipe Fitter
- Pilot
- Photographer
- Phlebotomy Technician
- Painter
- Nurse Practitioner
- Identifier
- Lacemaker
- HRD
- Hatter
- Host
- Herdsman
- Bouldering
- Assassin
- Bomberman
- Army
- Attendant
- Blogger
- Clergyman
- Cashier
- Botanist
- Bodyguard
- Aquascaping
- Assistant
- Electorate
- Physician
- Arbitrator
- Administrative